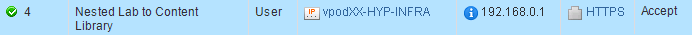Setting up NGINX as reverse proxy to allow vCenter Content Library subscription
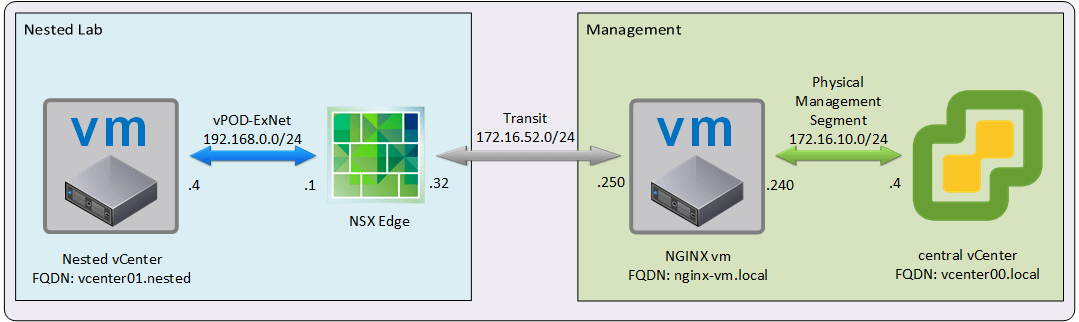
We want to setup a Content Library in our central vCenter and then allow the other vCenters in our Nested Labs to subscribe it without adding a lot of complexity to the configuration.
Requirements
- Allow only access to the Content Library URL
- Configuration need be able to support multiple nested vCenters subscribing the Content Library
- All Nested Environments use the same private address space
- Only NGINX vm (nginx-vm.local) should have an interface in both segments: “Transit” and “Physical Management”
Solution
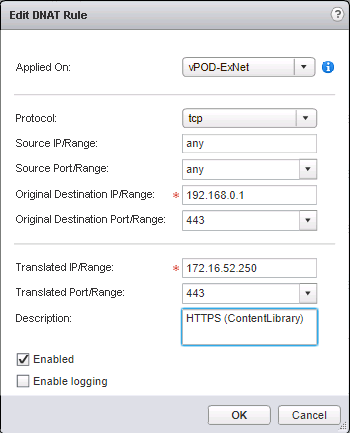
- First step will be setting up a DNAT and a FW Rule in each Nested Lab Edge to allow the nested vCenters to subscribe the Content Library using 192.168.0.1 (Nested Edge Internal Interface) instead of connecting directly to the central vCenter.
- Before we setup the NGINX we need to create a self-signed cert to be able to use SSL
openssl req -x509 -nodes -days 3650 -newkey rsa:2048 \
-keyout /etc/nginx/nginx-cert.key -out /etc/nginx/nginx-cert.cert
- Now we can setup the NGINX service, we will focus in the basic configuration to filter the URL to limit the access only to the Content Library vCenter service
Note: we assume that NGINX is installed in the vm already, since there are multiple ways and flavours to install it, depending on the engineer prefered distribution or prefered package management system.
user nginx;
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
# Load dynamic modules. See /usr/share/nginx/README.dynamic.
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 8096;
multi_accept on;
use epoll;
}
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 15;
types_hash_max_size 2048;
include /etc/nginx/mime.types;
default_type application/octet-stream;
# Load modular configuration files from the /etc/nginx/conf.d directory.
# See http://nginx.org/en/docs/ngx_core_module.html#include
# for more information.
include /etc/nginx/conf.d/*.conf;
# Settings for a TLS enabled server.
#
server {
# Listening only in the internal interface
listen 172.16.52.250:443 ssl http2 default_server;
server_name ngnix-vm.local;
ssl on;
ssl_certificate "/etc/nginx/nginx-cert.cert";
ssl_certificate_key "/etc/nginx/nginx-cert.key";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 30m;
# ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
access_log /var/log/nginx/https.access.log ;
# This is where we limit the URLs that we want to be available via reverse proxy
location ~ /cls/(data|vcsp)/* {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass https://vcenter00.local;
proxy_read_timeout 90;
proxy_redirect https://vcenter00.local https://$host ;
proxy_max_temp_file_size 0;
proxy_buffering off;
}
# Any URL that do not match the previous rule, will receive a HTTP 404
location ~ /* {
return 404 ;
}
error_page 404 /404.html;
location = /40x.html {
}
}
}
- Validating that everything works
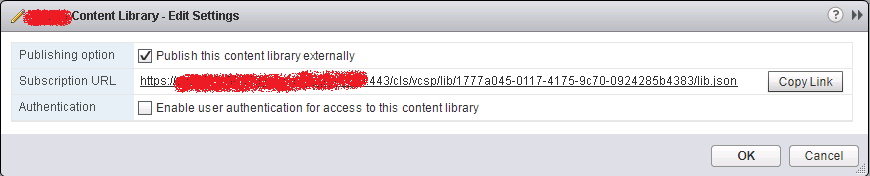
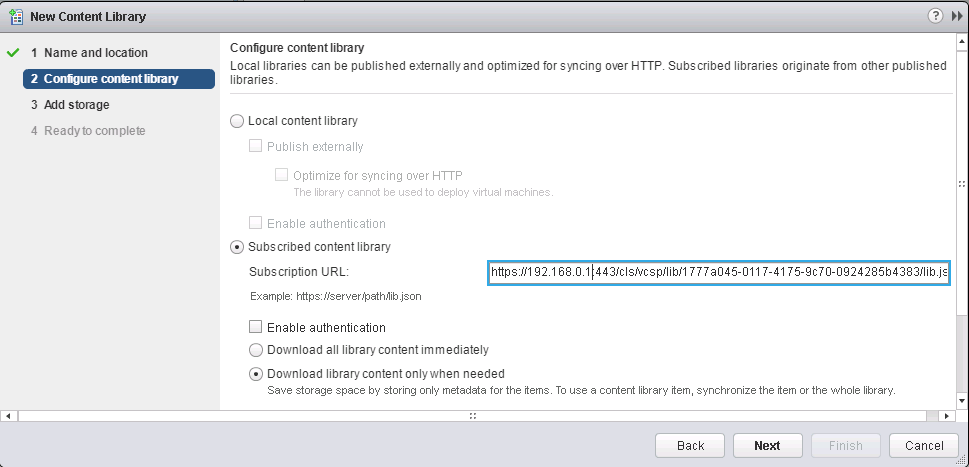
- Getting the Content Library link to subscribe
- Create new content library in vcenter01.nested via subscription of the one published by vcenter00.local
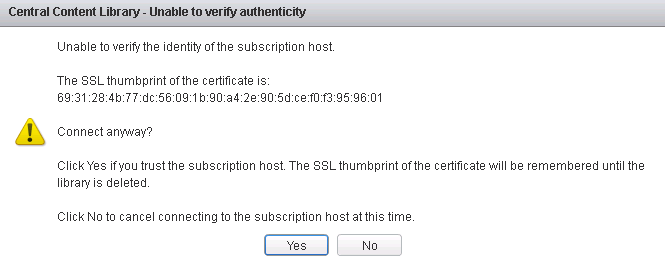
- Will prompt to accept the nginx-vm.local certificate
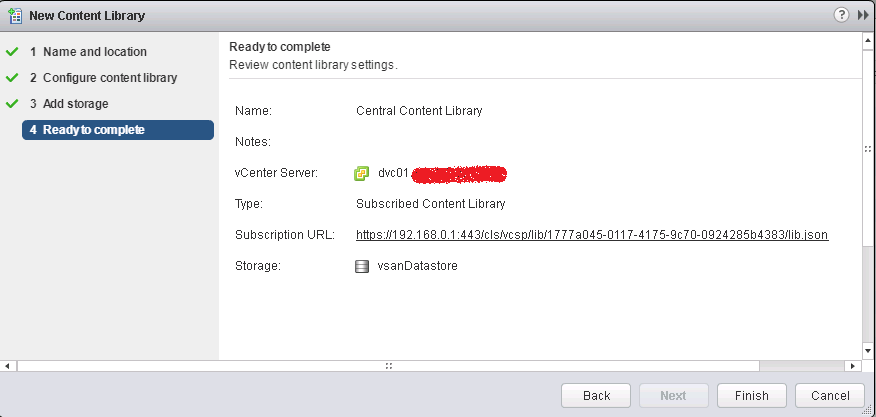
- Confirm all the details before click Finish
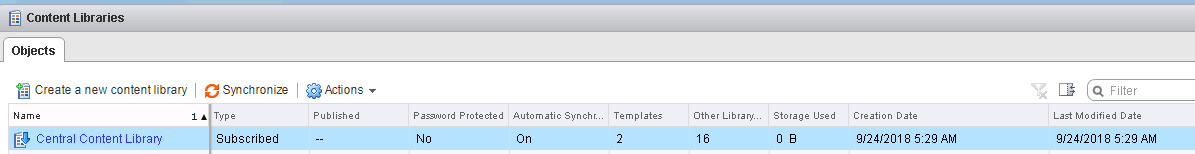
- And all done, since we configure the new Content Library to download content only when needed the initial footprint is quiet small